SSH works by installing SSH server and SSH application respectively on destination(remote) and source(Client) machine. After installing the SSH application on the client-side, you can provide information related to the remote server. On the server-side, There will be an SSH daemon that continuously checks for specific TCP/IP ports for client connection requests. Once the client initiates the connection requests with the right credentials, the SSH daemon starts exchanging the identification data with the client to establish a secured remote connection. You can log in to your remote SSH server by types:
Password Authentication Public Key Authentication (Passwordless)
In this tutorial, we will find out how to set up a Public key-based or passwordless SSH Login.
How to Setup Passwordless SSH Login
In passwordless or key-based authentication we create a pair of keys –
Private key: Stored securely and secretly on the client-side. Public key: Stored or given to the server that we want to access.
When we try to connect with a remote server using the authentication key, a message will be created by the public key based on the remote server. That message can only be read with the private key based on the client-server. After reading that message, the Client-server will send a response to the remote server to verify and establish the connection. Once you create and set up the keys, the entire process will be completed automatically.
How to create SSH Keys
So before we create a new key pair, let’s check once if you have already a key pair or not on your system, and for that, you can run the following command in your command line: If you find the keys then you can use them for the further process otherwise you can create new ones. To generate new key pair, open your command line and enter this code: Enter and accept the default location. Next, you will be asked for a passphrase. It depends on you that if you want it or not. If you do not want it then press Enter otherwise enter a passphrase for an extra layer of security. Also, not using a passphrase will help you in automating a lot of tasks. After hitting Enter, your keys will be created. You can list your keys with this command. Now as we have generated our keys, it’s time to copy the key on the remote server that you want to access. We will do this with the ssh-copy-id command. Type the following command on your command line: You will be asked for the remote_user password. Once you enter the correct password, the public key will be stored in the remote server. Now you can log in to your remote server without a password. Use the following command to establish a connection immediately:
How to disable Password Authentication
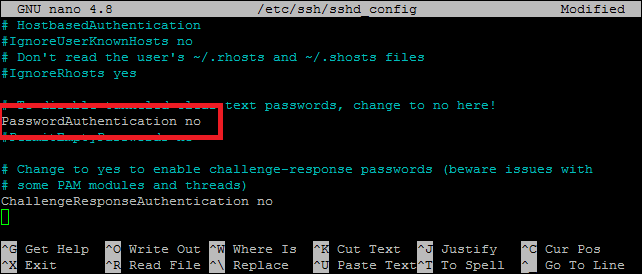
So as we have created our SSH keys, now we can disable the password authentication for security. Before disabling the password authentication, make sure you have stored the public key on your remote server and you are able to log in using the authentication key. To disable the password authentication, enter the following command and open SSH configuration files as a root user or sudo privileged user. Then search for the ‘password authentication’ line and modify it as follow:
After changing it, save your file and restart the SSH service. Now you will be able to login into the remote server without a password.
Conclusion
SSH is a secured and easy method to connect to a remote server. It is a simple and common Linux activity and you can learn it for your daily use. And you can even set up a passwordless SSH login by using authentication keys.